We get a lot of questions about security for many of our applications. This blog attempts to organize all the security features in one place and explains various levels of security.
- Security between Organizations
- Privileges using Roles
- Access Control at various levels
[more]
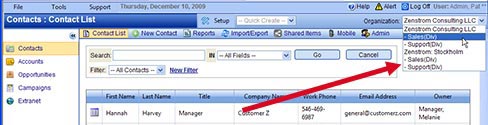
Security between Organizations
In OfficeClip applications you can create many independent organizations. For example, say you want to implement Contact Manager for two different divisions of your organization where the contacts are completely independent (i.e. they do not share anything). If you have such a requirement, you can add users only in the organizations they belong to. The rule is that the user who are not in the organization cannot have access to the organization data. You (as site administrator) can put yourself in both the organizations so that you can have access to contacts in both.
This kind of security is helpful where there are different parts of organization that works independently and simplified data security needs to be implemented.
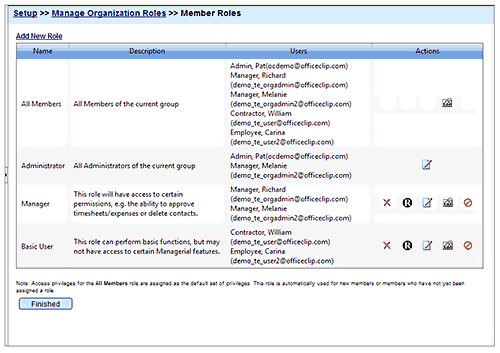
Privileges using Roles
Privileges allows you to switch off certain functionality in the software. These are the few steps in OfficeClip to implement privileges:
- Create a New Role, say Marketing Team
- Assign Role Privileges. For example, you may want to switch off the ability to Input New Contacts
- Assign users to the Role (Marketing Team)
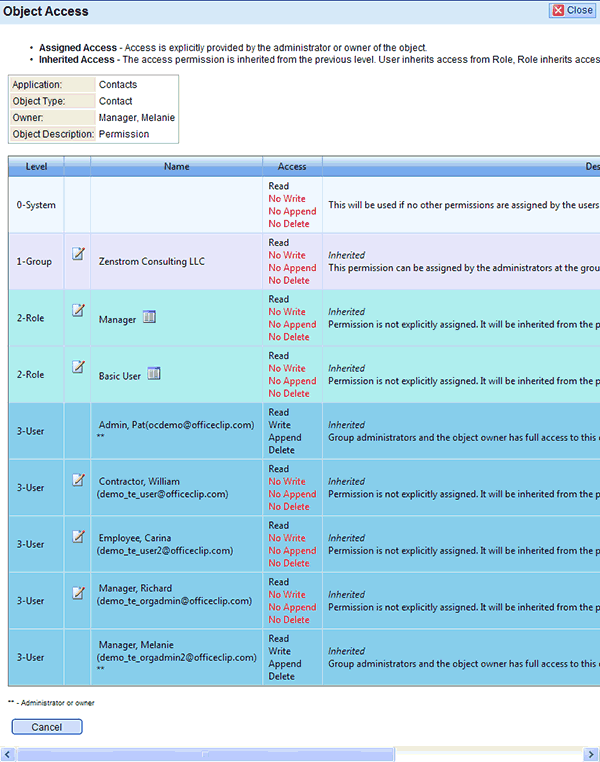
Access Control at various levels
Access control allows you to fine-tune security for any object in OfficeClip. Any piece of data (like a contact or a document) in OfficeClip is an object whose access can be controlled. There are various ways to control the access.
- Setting Default Access Rules for all objects in an organization
- Setting Access based on Roles
- Setting Access based on individual users
- Access control based on Rules
This has been a short introduction of various security levels in OfficeClip.
You can refer to the helpfiles for more information on Privileges.
There is also a pdf document that goes into little more detail: White Paper on Web-based Security
SK Dutta is a software architect and creator of OfficeClip Suite of products. He loves to design and develop software that makes people do their job better and more fun. He always explores ways to improve productivity for small businesses. He is also an avid reader in many areas, including psychology, productivity, and business.